What is this vulnerability?
I've found a lot of serious flaws on subdomain harvard.edu include severely errors(sql injection, Cross-site Scripting, local file disclosure) only by the use google search
What is the potential damage of this vulnerability?
1: sql injection
A SQL injection attack consists of insertion or "injection" of a SQL query via the input data from the client to the application. A successful SQL injection exploit can read sensitive data from the database, modify database data (Insert/Update/Delete), execute administration operations on the database (such as shutdown the DBMS), recover the content of a given file present on the DBMS file system and in some cases issue commands to the operating system. SQL injection attacks are a type of injection attack, in which SQL commands are injected into data-plane input in order to effect the execution of predefined SQL commands.
SQL Injection (SQLi) refers to an injection attack wherein an attacker can execute malicious SQL statements (also commonly referred to as a malicious payload) that control a web application’s database server (also commonly referred to as a Relational Database Management System – RDBMS). Since an SQL Injection vulnerability could possibly affect any website or web application that makes use of an SQL-based database, the vulnerability is one of the oldest, most prevalent and most dangerous of web application vulnerabilities.
By leveraging an SQL Injection vulnerability, given the right circumstances, an attacker can use it to bypass a web application’s authentication and authorization mechanisms and retrieve the contents of an entire database. SQL Injection can also be used to add, modify and delete records in a database, affecting data integrity.
To such an extent, SQL Injection can provide an attacker with unauthorized access to sensitive data including, customer data, personally identifiable information (PII), trade secrets, intellectual property and other sensitive information.
2: local file disclosure
Full Path Disclosure (FPD) vulnerabilities enable the attacker to see the path to the webroot/file. e.g.: /home/omg/htdocs/file/. Certain vulnerabilities, such as using the load_file() (within a SQL Injection) query to view the page source, require the attacker to have the full path to the file they wish to view.
3: Cross-site Scripting
Cross-site Scripting (XSS) refers to client-side code injection attack wherein an attacker can execute malicious scripts (also commonly referred to as a malicious payload) into a legitimate website or web application. XSS is amongst the most rampant of web application vulnerabilities and occurs when a web application makes use of unvalidated or unencoded user input within the output it generates.
By leveraging XSS, an attacker does not target a victim directly. Instead, an attacker would exploit a vulnerability within a website or web application that the victim would visit, essentially using the vulnerable website as a vehicle to deliver a malicious script to the victim’s browser.
Full Technical Analysis
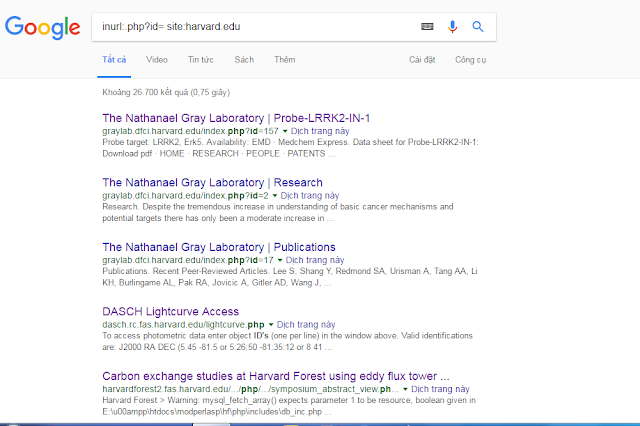
First I have found vulnerability Full Path Disclosure by google search
keyword: inurl:.php?id= site:harvard.edu
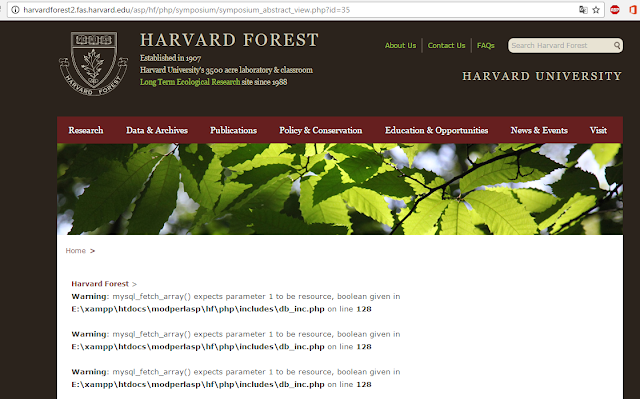
I find domain harvardforest2.fas.harvard.edu Full Path Disclosure
Warning: mysql_fetch_array() expects parameter 1 to be resource, boolean given in E:\xampp\htdocs\modperlasp\hf\php\includes\db_inc.php on line 128
i can read Full Path website E:\xampp\htdocs\modperlasp\hf\php\includes\db_inc.php from here I see harvard use xampp. it was a surprise to me. I do not think they use it
Next I want to find more vulnerabilities on harvardforest2.fas.harvard.edu i use burp suite scan
and a XSS flaw was found
this is quite common errors you can try at xss-game.appspot.com if harvard fixed
I intend to report to harvard but I forgot the link error Full Path Disclosure I do not want to use google to search again I'm on the link on the website but I did not find it, not .php in website only .html
i find link: http://harvardforest2.fas.harvard.edu/asp/hf/symposium/show_reu_symp.html I can add arbitrary content behind id,. at first I thought it was the system Vulnerabilitie xss I test and failed.
id function well with that I test it with sql injection. it was vulnerable sql injection time base







0 nhận xét:
Post a Comment